6.8 Understanding Rule Conditions
Each WebMarshal Rule or Rule Container includes one or more conditions. Not all conditions are available for all WebMarshal Rule types.
The complete list of conditions includes:
•When a web request is received for Direction
•Where the protocol/application is of type
•Except where the protocol/application is of type
•Where the URL is a member of Category
•Except where the URL is a member of Category
•Where the time of day is inside or outside of Schedule
•Where the server certificate is invalid
•Where the security protocol is
•Where the site requests a client certificate during SSL/TLS negotiation
•Where SSL/TLS could not be negotiated
•Where the content is/is not inspected HTTPS content
•Where the request contains cookies
•Where the header(s) match
•Where the URL domain name is an IP address
•Where the transferred data size is size
•Where the content matches all/any of TextCensor Script(s)
•Where the result of a malware scan is
•Where the file type is
•Except where the file type is
•Where the file is or contains a file of type
•Where the parent file type is
•Except where the parent file type is
•Where the file name matches
•Except where the file name matches
•Where the parent file name matches
•Except where the parent file name matches
•Where the download content type is
•Except where the download content type is
•Where an error occurs while unpacking
6.8.1.1 When a web request is received for direction
If this Condition is selected, the Rule will apply to all requests of the selected type (upload or download). Downloads include standard web page views and file access. Uploads include form and file posting. Click Direction to open the Data Direction window. Select Downloading or Uploading, and then click OK.
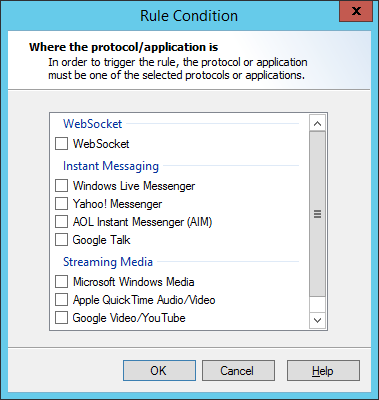
6.8.1.2 Where the protocol/application is of type
If this condition is selected, the Rule will apply for requests from specific Instant Messaging, Streaming Media, and WebSocket applications. Click Protocol/Application to open the Select Application window.

1.Select one or more applications to match by checking the boxes. To view the detailed description of the protocol, hover over an item.
2.Click OK to return to the parent Wizard.
You can specifically exclude applications using the exclusion condition Except where the URL is a member of Category.
6.8.1.3 Except where the protocol/application is of type
If this condition is selected, the Rule will not apply for requests from specific Instant Messaging, Streaming Media, and WebSocket applications listed in the Rule Description pane with this condition. Within a Rule, this condition overrides the condition Where the protocol/application is of type.
6.8.1.4 Where the URL is a member of category
If this Condition is selected, the Rule will apply for requests to all members of the URL Category (or Categories) listed in the Rule Description pane with the condition.
|
Note: URL matching is not case sensitive. |
Click Category to open the Select URL Categories window.
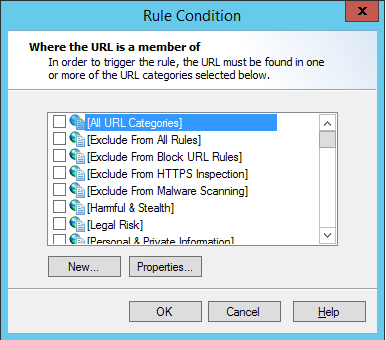
1.Select one or more URL Categories to match by checking the boxes. To view the detailed description of a category and the number of URLs it includes, select the category name and then click Properties.
2.Optionally click New to create a new URL Category.
3.Click OK to return to the parent Wizard.
You can specifically exclude URLs using the exclusion condition Except where the URL is a member of Category.
6.8.1.5 Except where the URL is a member of category
If this Condition is selected, the Rule will not apply for requests to any member of the URL Category (or Categories) listed in the Rule Description pane with this condition. Within a Rule, this condition overrides the condition Where the URL is a member of category.
See Where the URL is a member of category for details on how to select Categories to match.
Exception based rules are the key to good resource management. General rules should be created to cover most cases; exceptions should be made for small numbers of sites. For instance, a Rule might apply
Where the URL is a member of News Sites, except where the URL is a member of Tabloids.
You can use an exception condition alone (for instance, Where addressed to any URL, except where the URL is a member of Tabloids.)
6.8.1.6 Where the time of day is inside or outside of schedule
If this Condition is selected, the Rule will apply at specific times depending on the Schedule selected. Click Schedule to select a schedule using the Select Schedule window.
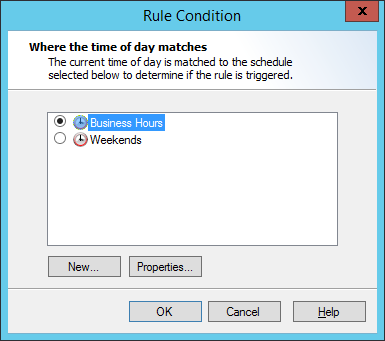
1.Select a Schedule to match using the radio buttons. To view or edit the details of a schedule, select the schedule name and then click Properties.
2.Optionally click New to create a new Schedule, as described in “Configuring Access Using Schedules”.
3.Schedule conditions normally match times within the schedule (blue area in the schedule policy element). If you want to match times outside the schedule, click inside and select Inside or Outside.
4.Click OK to return to the parent Wizard.
6.8.1.7 Where the server certificate is invalid
This condition allows you to apply a rule based on the validity conditions of a security certificate used by a HTTPS website. Click the Invalid link to open the Invalid Certificate window and select the certificate problems you want to check for.
1.Select one or more problems. If any of the problems occurs, the condition is met. WebMarshal can check for the following problems:
•Certificate is not valid for the web site: The certificate presented is not valid for the website (URL) the user is trying to access.
•Certificate has expired: The security certificate has expired.
•Certificate is not yet valid: The start of the certificate validity period has not been reached. Security certificates can have a future start date.
•Certificate is self-signed: The certificate has not been validated by a root certificate. It is validated only by the remote web server.
•Certificate chain is not trusted: The certificate cannot be chained back to a trusted root certificate, or WebMarshal does not recognize enough of the certificate chain.
•Certificate breaks certificate validation rules: The certificate does not conform to the industry standard for security certificates used to authenticate a website (typically due to usage constraints encoded in the certificate).
•Certificate is revoked: The certificate is marked as revoked by the issuer.
•Certificate revocation check failed: WebMarshal could not check the certificate revocation status. For more information about possible reasons see Help.
|
Note: Before you can use the two revocation options you must enable certificate revocation checking. See “Enabling Certificate Revocation Checking”. |
2.Click OK to return to the parent Wizard.
6.8.1.8 Where the security protocol is protocol
This condition allows you to check for the specific security protocol that was used for a HTTPS connection. The available protocols are distinguished by the difference in their cipher strength. The minimum protocol strength recommended is TLSv1.0.
|
Note: WebMarshal uses only TLSv1.0, TLSv1.1, TLSv1.2, or TLSv1.3 by default. SSLv2 connections are never allowed by the WebMarshal Proxy. SSLv3 connections are not allowed by default, but can be allowed. For information about how to change this default, see Trustwave Knowledge Base article Q20067. |
Click Protocol to open a window that allows you to select one or more protocols that connections can use. Select the protocols, and then click OK to return to the parent wizard.
|
Note: The protocol use for a connection is selected automatically from the available protocols. Generally the strongest protocol advertised by the remote web server is selected. You can use this condition if you want to block connections to web servers that do not support strong ciphers. You could also use this condition to create rule-based exceptions for sites that are required by your business but do not support best practice cipher strength. |
6.8.1.9 Where the site requests a client certificate during SSL/TLS negotiation
This condition allows you to take action when the remote web server requires the client browser to supply a security certificate, which will be used in addition to the server certificate. The client certificate uniquely identifies the user and can help to ensure security of a connection.
WebMarshal cannot inspect HTTPS content when a page requires a client certificate.
Use this condition with a rule action to block access, or to permit access without inspecting content.
|
Note: WebMarshal can only use the configured rule action if the request for a client certificate comes during the initial HTTPS negotiation. If the client certificate is requested later in the process, WebMarshal will block the request and return a special block page titled Client Security Certificate Required. |
6.8.1.10 Where SSL/TLS could not be negotiated
This condition allows you to take action when the user enters a HTTPS URL, but WebMarshal and the server cannot agree a security protocol.
|
Caution: If WebMarshal and the remote server cannot negotiate a protocol, traffic could be passed through uninspected. By default, this situation should be very rare since WebMarshal first negotiates any protocol and then checks the result to determine if the connection should be allowed. Best practice is to block all HTTPS connections where SSL/TLS could not be negotiated. |
6.8.1.11 Where the content is inspected HTTPS content
This condition can be used in a Standard or Content Analysis rule to determine if a request has been made from inside an inspected HTTPS connection. You can use this condition to apply different rules to data that WebMarshal has extracted from a HTTPS connection.
1.Click is to open a window that allows you to select from the following options:
Content is from inside an inspected HTTPS connection:
The request was made as a HTTPS connection that WebMarshal is inspecting.
Content is from a normal HTTP or non-inspected HTTPS connection:
The request was a standard HTTP request, or a HTTPS request that has not been decrypted by WebMarshal.
2.Click OK to return to the parent window.
6.8.1.12 Where the request contains cookies
This Condition allows you to apply Rules to download responses that send HTTP “cookies” as part of the response.
To apply this condition, select the box.
|
Note: WebMarshal does not currently check for request cookies (sent by the client). WebMarshal cannot check for cookies created by client-side action (such as JavaScript). |
6.8.1.13 Where the URL domain name is an IP address
This Condition, available in Standard rules, allows you to check for attempts to browse by IP address including IPv4 and IPv6 addresses.
|
Tip: Typically browsing by IP address is an attempt to circumvent the WebMarshal Rules. Most organizations will choose to block browsing by IP address for all users (with a few exceptions if necessary). |
6.8.1.14 Where the header(s) match
This Condition, available in Standard rules, allows you to check the existence and content of HTTP headers. Header matching can apply to request headers (sent by the client), response headers (sent by the server), or both. You can include one or more Header Match conditions in a single rule condition.
Click matches to open the Header Match Conditions window.
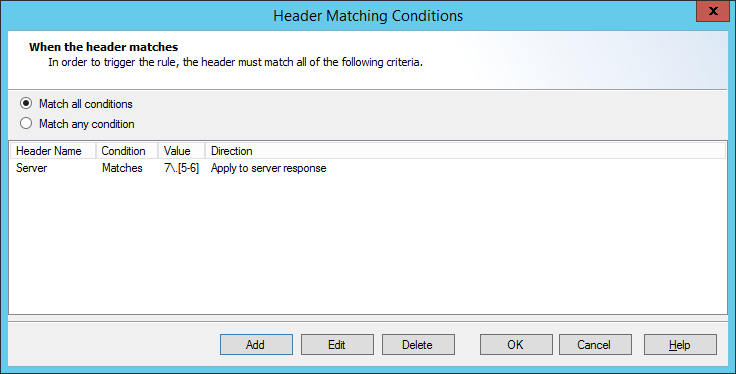
To begin choosing headers for matching, click Add. On the Add Item window, select the header name and define the action to perform.
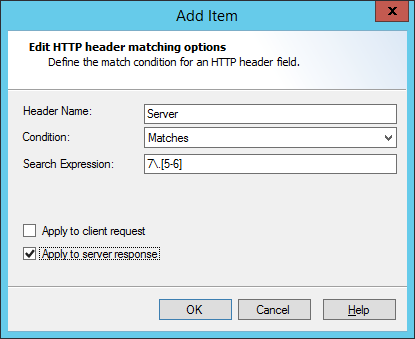
To change or remove the header matching actions, on the Rule Action window select an item and then click Edit or Delete. For more information, see Help.
6.8.1.15 Where the transferred data size is size
This Condition allows you to apply Rules based on the total size of a web request (sent or received). To choose file sizes, in the Rule Wizard click Size to open the Data Size window.
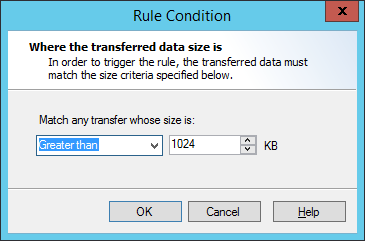
1.Choose whether to trigger on file transfers greater than or less than a specified size, or between two sizes.
2.Enter the size(s) in KB.
3.Click OK to accept changes and return to the parent Wizard. Click Cancel to revert to the saved information.
|
Note: WebMarshal only checks the total transfer size for each request (for instance, a HTML file, image, .zip file, or .wav file). WebMarshal does not check the sizes of individual files that could be unpacked from an archive. |
6.8.1.16 Where the result of a malware scan by scanner is
This condition invokes the scanners you select to check for viruses and other malware.
|
Note: WebMarshal can apply malware scanning to all types of files. You can limit scanning (for instance, you can choose not to scan image files), by using a file type or content type condition in the rule or rule container. Some files are generally safe (not known to contain malware payloads). Scanning all files provides added assurance but has a significant impact on performance and user experience. The WebMarshal default Access Policy includes two types of Malware scanning rules: •The standard scanning rules exclude common image types and text from scanning. •The “Extensive” rules scan all files. These rules are typically 2 to 4 times slower than the standard rules. |
To select scanners:
Click the hyperlink Scanners to open the Malware scanner used window.
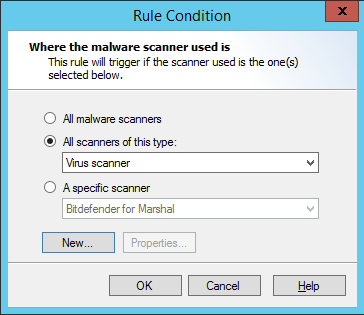
1.Choose which scanners to use. You can only select scanners you have configured in WebMarshal.
|
Note: If you have installed scanner software but you have not yet configured it, you can configure it by clicking New. |
•All malware scanners: This condition will check files using all configured scanners.
•A specific scanner: This condition will check files using a specific scanner. Use the menu to choose from the configured scanners. To view details of a selected scanner, click Properties.
2.Click OK to return to the parent Wizard.
To select scanner results:
Click the hyperlink Scanner result to open the Result of malware scan window.
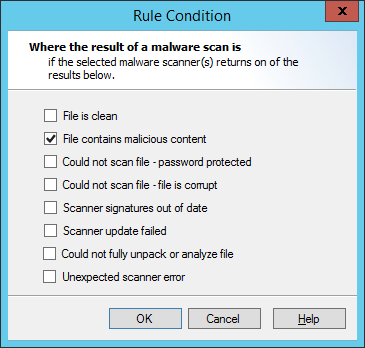
1.Check the boxes to select the desired conditions. In general, the more boxes selected, the more restrictive the conditions on downloads or uploads.
•File is clean: The condition will trigger if the file is reported as clean by all scanners selected within this rule condition.
•File contains malicious content: The condition will trigger if the file is reported to contain malware by any scanner selected within this rule condition. This is the basic condition.
•Could not scan file - Password protected: When this box is checked, the condition will trigger if any scanner reports the file as password protected.
•Could not scan file - File is corrupt: When this box is checked, the condition will trigger if any scanner reports the file as corrupt.
•Scanner signatures out of date: When this box is checked, the condition will trigger if any scanner reports its signature files are out of date.
•Scanner update failed: When this box is checked, the condition will trigger if the last update attempt for any scanner was unsuccessful.
•Could not fully unpack or analyze file: When this box is checked, the condition will trigger if any scanner reports that it could not unpack the file.
•Unexpected scanner error: When this box is checked, the condition will trigger if any scanner reports an unknown error or the code returned is unknown.
2.Click OK to return to the parent Wizard.
|
Note: Best practice is to block files that are reported as password protected or corrupt (since these cannot be scanned) as well as files containing malware. |
6.8.1.17 Where the content matches TextCensor script
This Condition invokes one or more TextCensor Scripts to check the text content of a web page or other text file.
|
Note: If a TextCensor Rule applies a “Permit” or “Block” action, all response text files which match the user group and other conditions are fully scanned before being returned to the user. If you have configured complex scripts, scanning can have an impact on perceived performance. To enhance processing speed, in most cases a TextCensor rule that blocks a request should also add the URL to a category. This allows WebMarshal to block future requests for the URL quickly, using a Standard rule. |
1.Select one or more Scripts to match by checking the boxes in the Select TextCensor Script window.
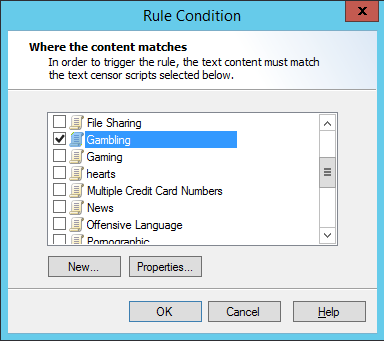
2.To create a new TextCensor Script, click New. For more information see “Identifying Web Content Using TextCensor Scripts”.
3.To review and edit an existing TextCensor script, select the script name and then click Properties.
If you have selected more than one TextCensor Script from the list., you can choose whether the content must match all, or any, of the selected scripts.
To choose an option:
1.Click All to open the Multiple Scripts window. Choose from the following
•Match all selected scripts: If you choose this option, the condition will only be true if all of the selected scripts trigger.
•Match any of the selected scripts: If you choose this option, the condition will be true if any of the selected scripts trigger.
2.Select an option, and then click OK to return to the parent Wizard.
6.8.1.18 Where the file type is
This Condition allows you to apply Rules to specific file types. File types are recognized by their internal structure, and not by their name or extension.
|
Caution: Although this condition is available in both Standard and Content Analysis rules, Trustwave recommends you use it only in Content Analysis rules. Standard Rules are often evaluated when only part of the data is available, and for many types this makes determining the type of the file unreliable. Content Analysis rules are always evaluated once the entire file has been downloaded and the file type has been correctly determined. For more information, see Trustwave Knowledge Base article Q12839. |
•In Standard rules, this Condition only checks the top level file that was directly requested.
•In Standard rules applied to uploads, this condition checks the type of files directly uploaded (attached to the upload form).
•In Content Analysis rules, this Condition checks the top level file and each file unpacked from archive files.
•For more file type matching options, see the Conditions Where the file is or contains a file of type and Where the parent file type is.
|
Note: You can match files in two other ways: •The Condition Where the file name is allows for file matching by name or extension. •The condition Where the content type is allows for file matching by the type declared in the web request headers. |
To choose file types:
1.Within the Rule Wizard click Type to open the Select File Types window.
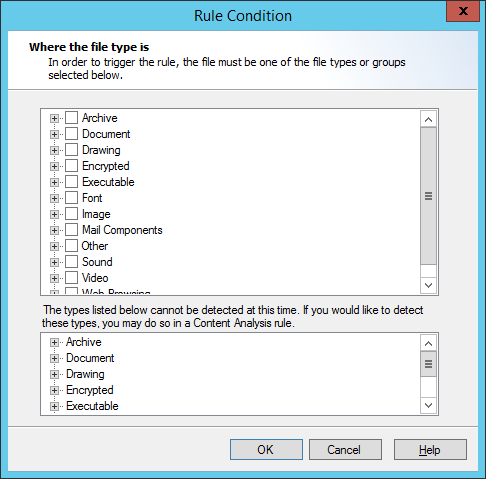
2.Expand any category to see the particular types available.
3.Choose the categories or specific types of files to match.
|
Note: Some types cannot be checked by Standard rules. The Select File Types window for Standard rules shows these types in the lower pane. You can check for these types in Quota or Content Analysis rules. |
4.Click OK to accept changes and return to the parent Wizard. Click Cancel to revert to the saved information.
6.8.1.19 Except where the file type is
This Condition allows you to apply Rules to all files that are not of specific file types. Before using this condition in Standard Rules, see the note to “Where the file type is”.
•In Standard rules, this Condition only checks the top level file that was directly requested.
•In Standard rules applied to uploads, this condition checks the type of files directly uploaded (attached to the upload form).
•In Content Analysis rules, this Condition checks the top level file and each file unpacked from archive files.
•For more file type matching options, see the Conditions Condition Where the file is or contains a file of type and Where the parent file type is.
To choose file types to exclude, within the Rule Wizard click Type to open the Select File Types window. See the condition Where the file type is for details on how to select types.
6.8.1.20 Where the file is or contains a file of type
This Condition allows you to create Content Analysis Rules that check a condition for a file that was requested, or all files that are contained within it (if it is a document or archive that WebMarshal can unpack). For instance, you can apply a rule to document files that contain images. For other options, see the condition Where the parent file type is.
To choose file types to match, within the Rule Wizard click Type to open the Select File Types window. See the condition Where the file type is for details on how to select types.
You can choose to include or exclude the originally requested file from matching.
To choose an option:
1.Click is or contains to open the Trigger window. Choose from the following
•The transferred file or any unpacked file: If you choose this option, the condition will consider the type of the originally requested file, and any files unpacked from it.
•Any unpacked file: If you choose this option, the condition will ONLY consider the type of unpacked files, and will not consider the type of the originally requested file.
2.Select an option, and then click OK to return to the parent Wizard.
|
Tip: For example, if you want to make a rule that applies to all image files, including image files within documents or archives, select The transferred file or any unpacked file. If you want to make a rule that applies to image files within documents or archives, but NOT directly requested images, select Any unpacked file. •If you combine this condition with other conditions, such as a file name condition, the other conditions are evaluated on the main file and NOT on contained files. |
6.8.1.21 Where the parent file type is
This Condition allows you to create Content Analysis Rules that apply to a file that was unpacked from an archive or other unpackable type, depending on the type of the parent file.
|
Note: For other file type conditions, see Where the file is or contains a file of type, Where the file type is, and Except where the file type is. |
To choose file types to match, within the Rule Wizard click Type to open the Select File Types window. See the condition Where the file type is for details on how to select types.
You can choose to perform matching on the originally requested file, all unpacked files, or only the immediate parent container.
|
Tip: You can use this condition in combination with other conditions that apply to the unpacked file. For instance, you can apply a rule where the parent file type is ZIP and the file type is DOC. If you combine this condition with other conditions, such as a file name condition, the other conditions are evaluated on the child file and NOT on any parent files. |
To choose an option:
1.Click the immediate to open the Checks window. Choose from the following
•The immediate parent file: If you choose this option, the condition will consider the type of the file that explicitly contains the unpacked file.
•The top-level parent file: If you choose this option, the condition will consider the type of the originally requested file (that contains the unpacked file, perhaps within other archives).
•Any parent file: If you choose this option, the condition will consider the type of each file in the set of archives.
2.Select an option, and then click OK to return to the parent Wizard.
|
Tip: Suppose you click a link to archive1.zip. archive1.zip contains archive2.cab, and archive2.cab contains data.txt archive1.zip>>archive2.cab>>data.txt •archive1.zip is the top level parent. •archive1.zip is the immediate parent of archive2.cab. Both archive1.zip and archive2.cab are the any level parents of data.txt. |
6.8.1.22 Except where the parent file type is
This Condition allows you to apply Rules to a file that was unpacked from an archive, if the parent files in the archive are not of specific file types.
To choose file types to match, within the Rule Wizard click Type to open the Select File Types window. See the condition Where the file type is for details on how to select types.
You can choose to perform matching on the originally requested file, all unpacked files, or only the immediate parent container. To choose a matching option, click the immediate to open the Checks window. See the condition Where the parent file type is for details of the options on this window.
6.8.1.23 Where the file name matches
This Condition allows you to apply Rules to files with specific names or extensions. This condition is useful to allow specific files, or to block text files that WebMarshal cannot recognize by their structure or content-type header.
|
Note: You can match files in two other ways: •The condition Where the content type is allows for file matching by the type declared in the web request headers. •The condition Where the file type is allows for file matching by internal structure of files. |
To choose file types, within the Rule Wizard click Name to open the Enter File Names window.
The * wildcard is supported (* matches any number of characters; for instance, *.exe matches any exe file).
1.To add a name to the list, click Add, and then enter the desired name or wildcard string to match partial names. Press Enter or click away from the name when done.
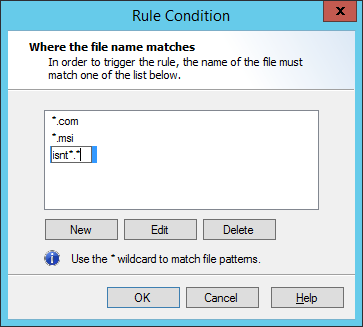
2.To edit an existing name, select it and then click Edit.
3.To delete an existing name, select it and then click Delete.
4.Click OK to accept changes and return to the parent Wizard. Click Cancel to revert to the saved information.
Except where the file name matches
This Condition allows you to apply Rules to all files that are not specific file names.
To choose file names to exclude within the Rule Wizard click Name to open the Except where the file name matches window.
The * wildcard is supported (* matches any number of characters; for instance, *.exe matches any exe file).
1.To add a name to the list, click Add, and then enter the desired name or wildcard string to match partial names. Press Enter or click away from the name when done.
2.To edit an existing name, select it and then click Edit.
3.To delete an existing name, select it and then click Delete.
Click OK to accept changes and return to the parent Wizard. Click Cancel to revert to the saved information.
6.8.1.24 Where the parent file name matches
This Condition allows you to apply Rules to a file that was unpacked from an archive or other unpackable type, depending on the name of the parent file.
|
Note: For other file type conditions, see Where the file is or contains a file of type, Where the file type is, and Except where the file type is. |
To choose file names to match, within the Rule Wizard click Name to open the Select File Names window. See the condition Where the file name matches for details of this window.
You can choose to perform matching on the originally requested file, all unpacked files, or only the immediate parent container.
To choose an option:
1.Click the immediate to open the Checks window. Choose from the following
•The immediate parent file: If you choose this option, the condition will consider the name of the file that explicitly contains the unpacked file.
•The top-level parent file: If you choose this option, the condition will consider the name of the originally requested file (that contains the unpacked file, perhaps within other archives).
•Any parent file: If you choose this option, the condition will consider the name of each file in the set of archives.
2.Select an option, and then click OK to return to the parent Wizard.
Example: Suppose you click a link to archive1.zip. archive1.zip contains archive2.cab, and archive2.cab contains data.txt
archive1.zip>>archive2.cab>>data.txt
•archive1.zip is the top level parent.
•archive1.zip is the immediate parent of archive2.cab.
Both archive1.zip and archive2.cab are the any level parents of data.txt.
6.8.1.25 Except where the parent file name matches
This Condition allows you to apply Rules to a file that was unpacked from an archive, if the parent files in the archive do not match specific names or extensions.
To choose file names to match, within the Rule Wizard click Name to open the File Names window. See the condition Where the file name matches for details of this window.
You can choose to perform matching on the originally requested file, all unpacked files, or only the immediate parent container. To choose a matching option, click the immediate to open the Checks window. See the condition Where the parent file name matches for details of the options on this window.
6.8.1.26 Where the download content type is
This Condition allows you to apply Rules to specific content types. Content types are recognized by the header information of the web request. Content type information is only available for downloads (not uploads or postings). The web browser uses the content type information to determine how to display the content, or what helper application to invoke. For instance, a PDF document with content type application/pdf usually opens in a PDF plug-in or reader.
|
Note: You can match files in two other ways: •The Condition Where the file name is allows for file matching by name or extension. •The condition Where the file type is allows for file matching by the internal structure of the file. |
To choose content types, within the Rule Wizard click Type to open the Select
Content Types window.
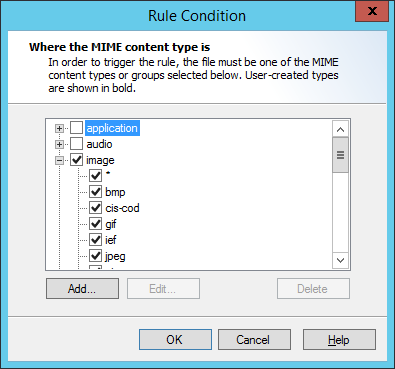
1.Expand any category to see the particular types available.
2.Choose the categories or specific types of files to match.
3.To match a type not in the list, click Add. Enter the new type and optional subtype (for instance, application/x-my-application) and then click OK. The new type is permanently added to the list of types you can select.
Click OK to accept changes and return to the parent Wizard. Click Cancel to revert to the saved information.
6.8.1.27 Except where the download content type is
This Condition allows you to apply Rules to all files that are not of specific content types. Content type information is only available for downloads (not uploads or postings).
To choose content types to exclude, within the Rule Wizard click Type to open the Select Content Types window. See the condition Where the content type is for details on how to select types.
6.8.1.28 Where an error occurs while unpacking
This Condition allows you to check for archive and document files that WebMarshal cannot unpack. You may want to block files that cannot be unpacked, or notify the administrator.
To apply this condition, select the box.