This article applies to:
- MailMarshal 11.2 and above
- MailMarshal SPE 4.4 and above
- Entra ID Group Import
Question:
- How do I register an application in Azure/Entra to allow group import to MailMarshal?
- What are the options and requirements for use of imported Entra groups?
Background:
MailMarshal allows you to retrieve user group information directly from Microsoft Entra ID (formerly known as Azure Active Directory). To connect, you must create an "application" in Entra.
You will enter the Client ID, Tenant ID, and Secret from Entra in the MailMarshal Management Console or the MailMarshal SPE Customer Console
Procedure:
Note common missed items in this procedure:
- MailMarshal uses the Array Manager REST API SSL certificate to access a local process that connects to Entra. If the certificate has expired, use the MailMarshal Server Tool to generate a new one. Include localhost in the list of SANs.
- Be sure you grant Application permissions (not "delegated")
- Be sure to grant admin consent
- Log in to the Microsoft Entra Admin Center (entra.microsoft.com). The minimum required permission is "Cloud Application Administrator"
- If you have access to more than one tenant, use the Settings menu (gear icon in the top bar) to switch to the specific tenant.
- From the left menu browse to Identity > Applications > App registrations. Click New registration.
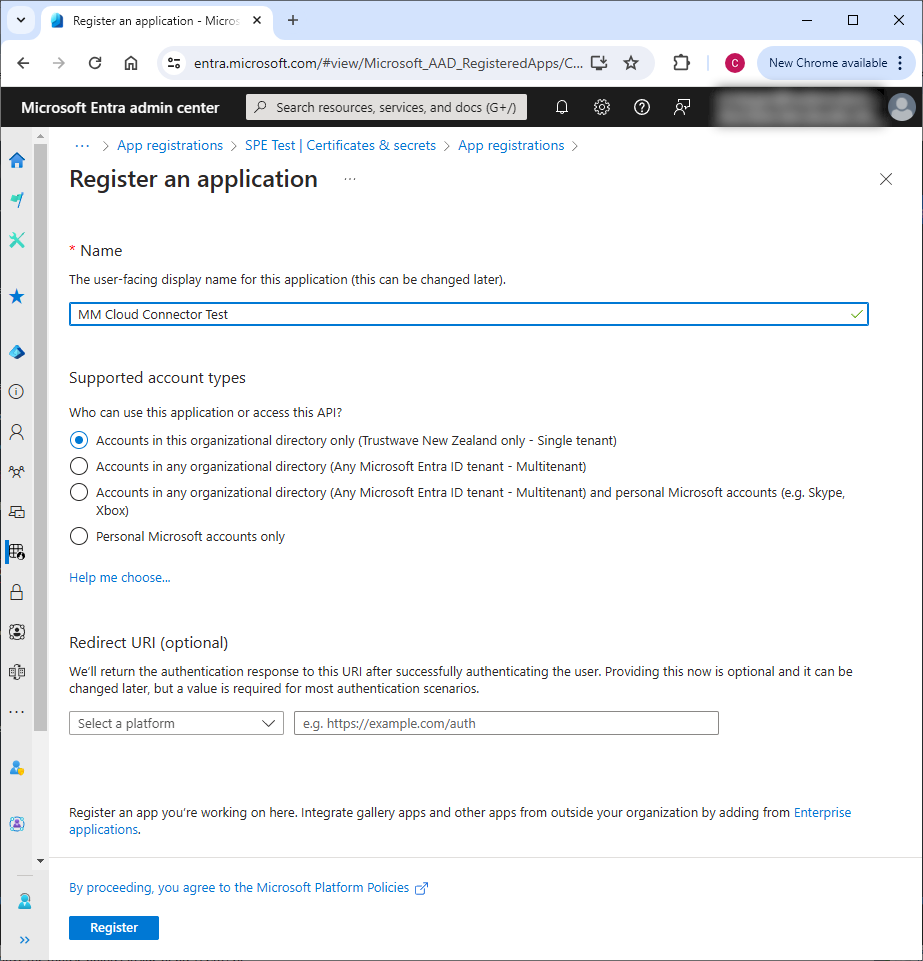
- Enter a name.
- For "supported account types" accept the default (single tenant).
- Click Register.
- From the overview page of the application, note the following values:
- Application (client) ID
- Directory (tenant) ID
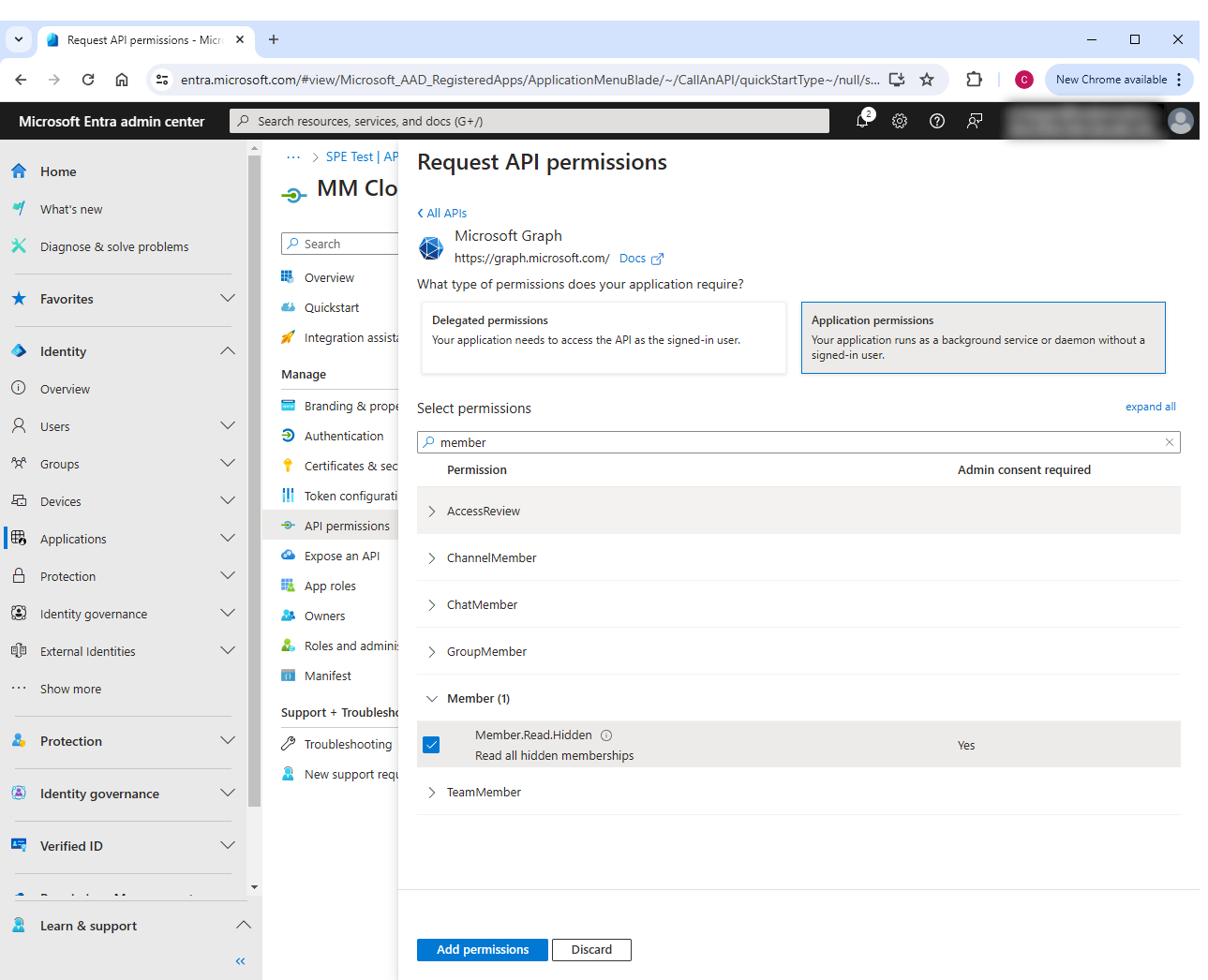
- From the API Permissions page of the application, grant the following Microsoft Graph permissions (Application permissions):
- Group.Read.All
- Member.Read.Hidden
- OrgContact.Read.All
- User.Read.All
- After updating the above permissions, click Grant admin consent (above the list of permissions)
- From the Certificates & Secrets page of the application, create a new client secret. Note the value (it is only available immediately after creation).
Use the Client ID, Tenant ID, and client secret on the Entra Properties tab of the Connector page in the MailMarshal Management Console, or the Entra Connector Properties page in the SPE Customer Console.
Group usage:
After creating the connector you can select groups to import using the Import Connector Group or Import Entra Groups button on the User Groups page.
Groups are populated immediately. Group membership is queried and updated hourly.
-
