This article applies to:
- Trustwave MailMarshal (SEG)
Question:
What are some examples of creating header re-write rules?
Information:
These examples have been compiled to assist with the creation of header re-write rules. They can be used as is or modified to suit, depending on individual needs.
Caution! Header Re-Write rules are extremely powerful. Test any rules thoroughly, as errors can cause all affected messages to be undeliverable.
For full documentation on the Regular Expression syntax see Knowledge Base article Q10520. Additional information is available in the User Guide.
User interfaces differ slightly in newer releases of MailMarshal, but the functionality described is identical.
Variables:
MailMarshal variables can be used in the substitution string. For example, you can insert the sender email address by using the variable {sender} - This function provides a limited ability to rewrite one header field based on the content of another field, particularly when used with map files. See the "Sender based routing" example below.
Re-write the domain information:
- Select fields to match against: "Received"
- Select "Entire Line" as the Field Parsing method
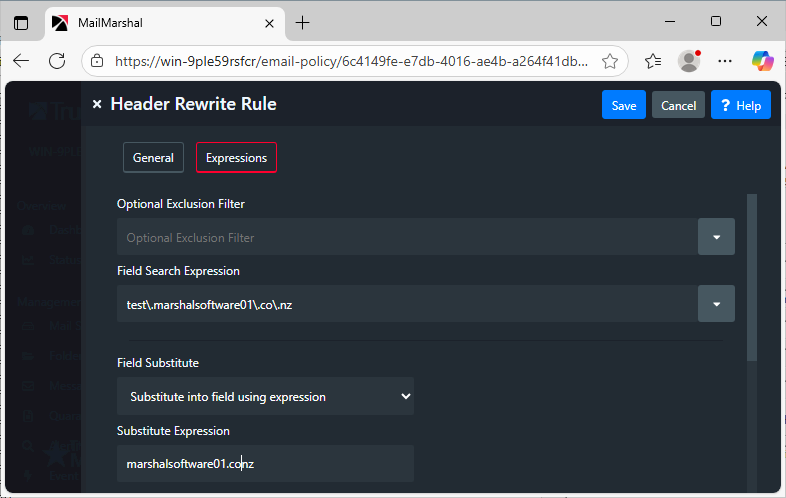
This rule will re-write
from test.marshalsoftware01.co.nz (not verified[172.28.1.1]) by marshalsoftware02.co.nz
to
from marshalsoftware01.co.nz (not verified[172.28.1.1]) by marshalsoftware02.co.nz
Re-write or delete the IP information:
- Select the fields to match against: "Received"
- Select the Field Parsing method "Entire Line"
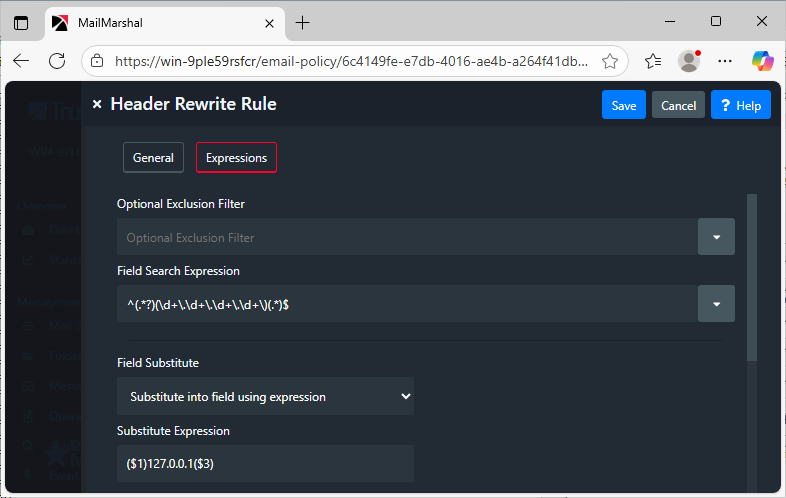
This rule will re-write
from test.marshalsoftware01.co.nz (not verified[172.28.1.1]) by marshalsoftware02.co.nz
to
from test.marshalsoftware01.co.nz (not verified[127.0.0.1]) by marshalsoftware02.co.nz
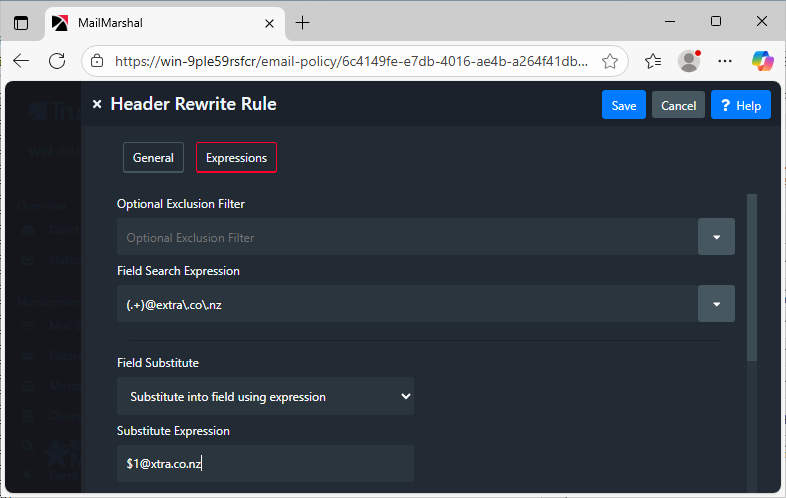
Rewrite 'extra' to 'xtra':
(A common typographical or autocorrect error when entering this domain name) - Select the fields to match against: "Envelope Recipient" and "To"
- Select Filed Parsing Method: "Email Address"
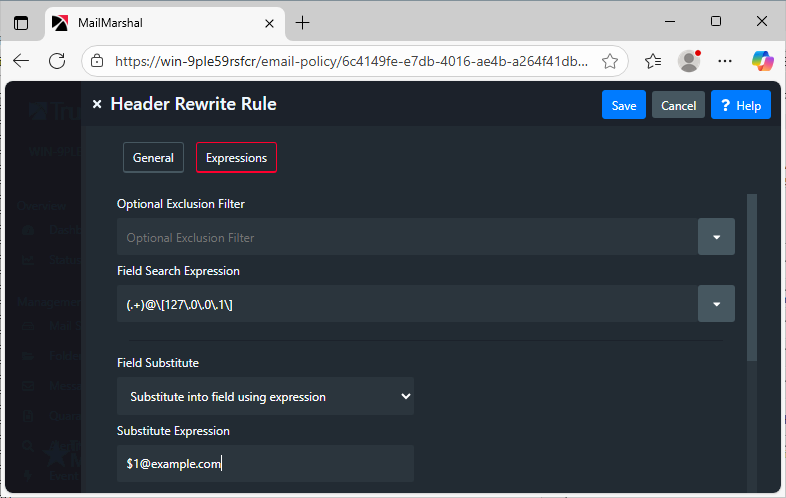
Rewrite Domain Literal Addresses:
"I believe the e-mail address (admin@[x.x.x.x] - where x.x.x.x is the IP address associated with the domain) is RFC compliant, but it is rejected by MailMarshal as being invalid."
- Select the fields to match against: 'Envelope Recipient' and 'To'.
- Select 'Entire Line' as the Field Parsing Method.
Usage of the MAP file option:
Mapping using a file allows a level of indirection in resolving what to substitute into the field. A map file must be plain text; each line of the file must contain a key and value pair separated by a comma. For example:
john@domain.co.uk,john@domain2.co.uk
peter@domain.co.uk,peter@host1.domain.co.uk
The first entry in the line is a lookup key. The second value is the result to be substituted in place of the original field when the key is matched (e.g. for a search expression of $1@domain.co.uk would, for the input string john@domain.co.uk, return john@domain2.co.uk). If the key value is not found in the map file then it is returned unchanged as the result.
If you enter a relative path in the filename field, MailMarshal evaluates the path relative to the install directory. Trustwave recommends a relative path such as NodeConfig\theMapFile.txt
- Note: When you first create the file you must manually place a copy in both the NodeConfig directory and the Config directory within the MailMarshal installation on the Array Manager. The Configurator interface checks the NodeConfig directory for the presence of the file and uses this location for testing, but replication to processing nodes uses the Config directory. To make changes, normally edit only the file in the Config directory.
- If the Array Manager does not include processing services you must manually create the NodeConfig directory and in this case to test changes you must update the copy in that location manually.
Append the domain to a badly formatted email address:
Field substitution allows you to substitute into a matched field using a sed or perl-like syntax.
- Select the fields to match against: 'Envelope return path'
- Select Field parsing method: 'Entire Line'
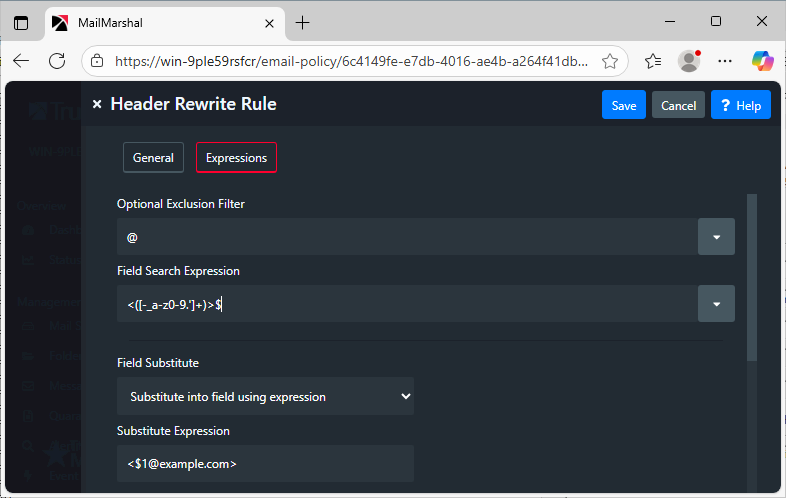
The rule will re-write <username> to <username@example.com>
Sender based routing with variables and MAP file:
It is possible to route a message based on the sender, using two rules, variables and a map file. This is an advanced usage and the specific requirements will vary.
- In the first rule, rewrite the Envelope Recipient (and the visible To: if desired), and set the value using the {Sender} variable
- For example use Substitute expression: {Sender}.rewrite.local
- In the second rule, use a map file to rewrite the fields again and set the actual desired recipient based on the temporary value
- Search expression: (.*)\.rewrite\.local
- Map using file with lookup key $1
- This article was previously published as:
- NETIQKB29651
- Marshal KB340