This article applies to:
- MailMarshal (SEG)
- Current updates to file unpacking
Symptoms:
- Email containing Microsoft Office documents is blocked by the default "double extension" rule
Causes:
- Current versions of the MailMarshal file unpacker extract certain files from Microsoft Office docs with names that trigger this rule.
- Due to the evolution of malware in Microsoft Office documents, LevelBlue believes it is important to present all extracted contents from these documents to the various layers of protection in MailMarshal.
- Default rules in new installations of current versions of MailMarshal include the "double extension" rule, but it is disabled by default.
Resolution:
To avoid the rule triggering on Office documents, you can exclude the child files extracted from these documents from the double extension check.
- Within the double extension rule, add a condition Where attachment parent is of type…
- Select "Where parent container is not of type:"
- Select any problem parent types such as Excel 2007+ or Word 2007+ document.
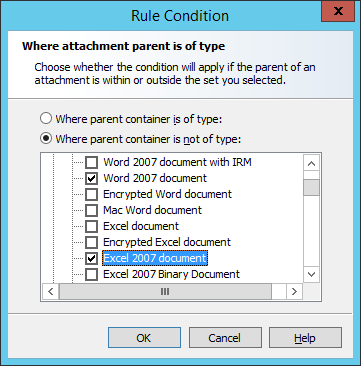
- The rule description will then appear similar to the following:
When a message arrives
Where message is incoming
Where message contains attachments named '*.??.??' or '*.??.???' or '*.??.????' or '*.???.??' or '*.???.???' or '*.???.????'
And where attachment parent is not of type: 'DOCX' or 'XLSX'
Send a 'File Extension in' notification message
And move the message to 'Suspect' with release action "continue processing" - Remember to commit configuration.
Notes:
The "double extensions" check is designed to block files that try to hide their type from Windows users. Although this check can be valuable, it is also prone to false positives. Legitimate files can be named with multiple dots (for example a log file could be named application.jun25.log)