This article applies to:
Question:
- Does Trustwave SWG protect against the insecure library loading vulnerability?
Answer:
The vulnerability described in Microsoft Security Advisory 2269637, involves using a legitimate application to preload malicious library files from remote sources, including SMB shares and WebDAV. For example, an audio/video player application might be tricked into loading malware that poses as a codec DLL. This technique is sometimes called “DLL hijacking”.
Although SMB falls outside of the scope of secure web gateway solutions, SWG appliances can prevent client applications from using WebDAV to retrieve malicious libraries from the Internet. By default, SWG appliances include a rule named Block Binary Objects without a Digital Certificate. Since malware authors do not sign their code, this rule by itself blocks exploits based on this vulnerability.
In some environments, it is preferable to permit downloading of unsigned binaries, so the Block Binary Objects without a Digital Certificate rule is sometimes disabled or placed in X-Ray mode. In this situation, it is still possible to define a policy that prevents attempts to exploit this vulnerability via WebDAV. Doing so involves preventing WebDAV downloads of .dll and .ocx files. The procedure for creating the appropriate lists and rule is detailed below.
- Log in to the SWG web interface.
- Navigate to Policies -> Condition Settings -> File Extensions.
- Right-click the File Extensions folder and select Add Component.
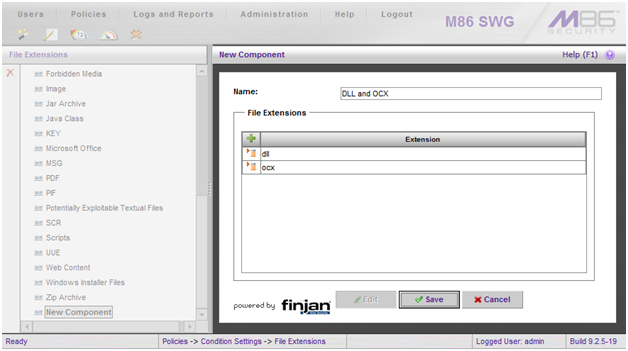
- Define a name for the new list.
- Click the green + to add an entry. The value for the entry should be: dll
- Click the green + to add an entry. The value for the entry should be: ocx
- Click the Save button. The screenshot below illustrates the new entry.
- Navigate to Policies -> Condition Settings -> Header Fields.
- Right-click the Header Fields folder and select Add Component.
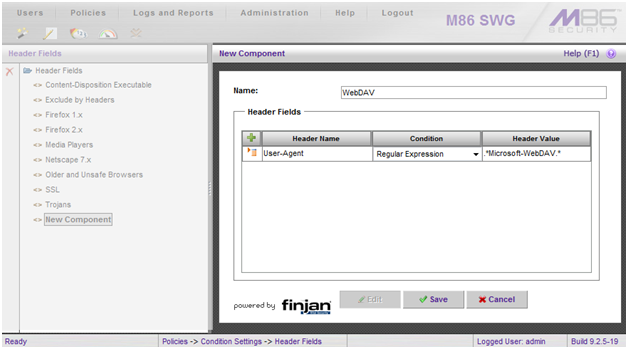
- Define a name for the new list, and click the green + to add an entry. The values for the entry should be:
Header Name: User-Agent
Condition: Regular Expression
Header Value: .*Microsoft-WebDAV.*
- Click the Save button. The screenshot below illustrates the new entry.
- Navigate to Polices -> Security -> Advanced and expand the tree so that the rules under the active security policy are visible.
- Right-click the rule above which the new rule will be inserted. For policies based on the Finjan Medium Security Policy, the new rule will typically be inserted above Allow Whitelisted ActiveX, Java Applets and Executables.
- Choose the Insert New Rule option.
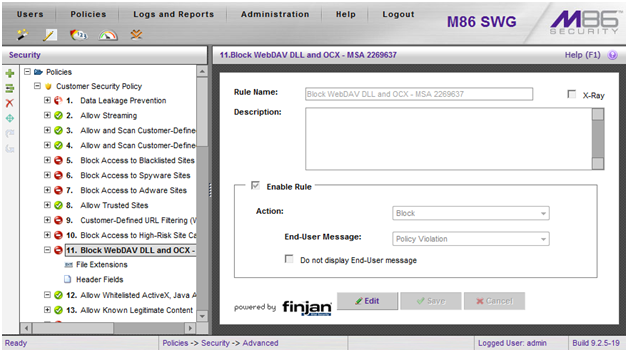
- Define a name for the rule, make sure that the Action is set to Block and an appropriate End-User message is selected.
- Click Save.
- Right-click the new rule and click Add Condition.
- In the Condition Name picklist, select File Extensions. Select the checkbox for the new File Extensions list that you created, and click Save.
- Right-click the new rule and click Add Condition again.
- In the Condition Name picklist, select Header Fields. Select the checkbox for the new Header Fields list that you created, and click Save.
- If you click on the new rule name in the left pane, it should appear similar to the screenshot below. If this is the case, please commit the changes.
Notes:
- If more than one policy is in use, it will be necessary to repeat Steps 13 – 20 for each policy that should include this rule. Please commit when all of the modifications are finished.
- Some sites might have legitimate reasons for accessing DLL and OCX files via WebDAV. Exceptions can be implemented on a case-by-case basis by using other policy elements, such as URL Lists.