This article applies to:
- Trustwave MailMarshal (SEG)
- Note for MailMarshal (SEG) 10.0 and above additional steps are required for same-server installation and some restrictions may apply
- Microsoft Exchange Server 2019, 2016, 2013 and "Subscription Edition"
- For Exchange Online, see the document "Using Trustwave MailMarshal with Exchage Online", available on the MailMarshal documentation page.
Question:
- How to configure Trustwave MailMarshal (SEG) to forward mail to Microsoft Exchange Server
- How to configure Microsoft Exchange Server to forward and receive email from Trustwave MailMarshal (SEG)
Procedure:
To configure MailMarshal as gateway with Microsoft Exchange Server (current versions) as the internal email server, follow the steps in this article.
- MailMarshal (SEG) 8.X interfaces differ, but the information required is the same.
Please read through and understand the details, particularly about port assignments, before starting.
NOTES: - It is possible to install Trustwave MailMarshal with Exchange Server on the same machine and this article covers this scenario. However, you should carefully consider the resources required for same-server installation.
- For installations of significant size, Trustwave recommends you install MailMarshal separately. This article also covers installation of MailMarshal on a separate machine with email flow between the servers.
- The MailMarshal Array Manager includes a default HTTPS website that conflicts with Exchange. To install MailMarshal on the same server as Exchange you must change the binding of the MailMarshal Management Console. The Exchange ECP and OWA websites will not run until you make this change. Current MailMarshal installers detect conflicts and prompt you to select a different port.
- For additional steps to allow the co-existence of MailMarshal and Exchange websites, see article Q12671.
- Port 25 assignment: When installing Trustwave MailMarshal and Exchange server on the same computer, you will most likely find that both attempt to use port 25 for SMTP email. Generally you should allow MailMarshal to use this port (to accept email from external locations) and configure Exchange to use another port. Port 97 is usually available for this purpose.
- Exchange connectors by default use TLS. To learn about configuring TLS in MailMarshal, see article Q11636.
- This article describes the simplest un-authenticated configuration for incoming email. Many other security options are available.
- For example, you may want to limit access by IP address, and/or use Basic authentication over TLS to control access.
- Two procedures are given for configuring MailMarshal delivery. The first is for the configuration of MailMarshal if it has not already been installed. The second can be used to change the settings after MailMarshal is already installed.
Configuring MailMarshal Delivery During Initial Installation
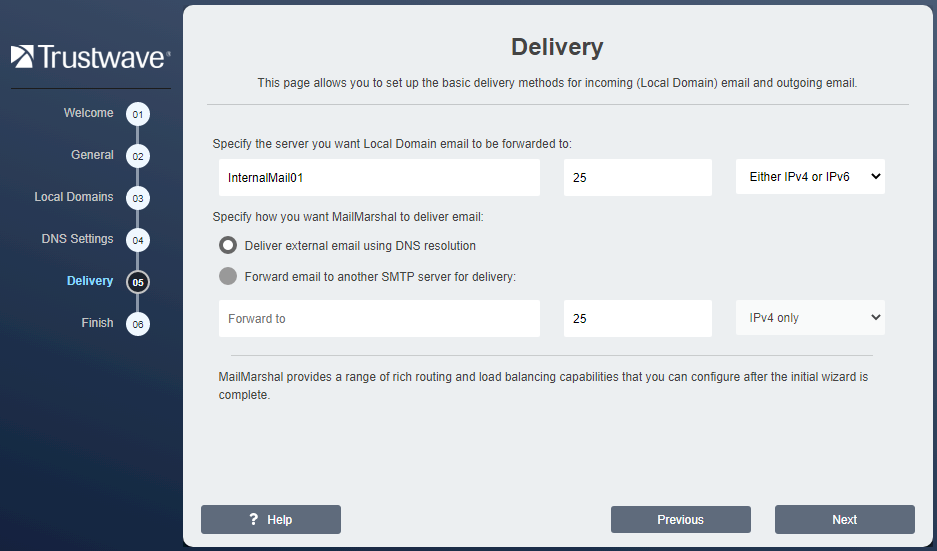
- In the Configuration Wizard, on the Delivery window Specify the Server... field, enter the IP Address or Server Name and the Port of your Microsoft Exchange Server.
- If Exchange and MailMarshal are on the same server, be sure to configure and use a unique port for Exchange, as mentioned above.
- Select Deliver external email using DNS resolution. See below.
Configuring MailMarshal Delivery After Installation:
- In the Management Console, expand System Configuration > Array Properties and select Routes.
- Edit the Default Routing Table.
- Edit the Local Domain you would like to forward to Microsoft Exchange Server.
- On the Domain Routing window double click the IP Address you are currently using to route mail.
- On the Route Entry Properties window, change the IP address to the IP Address of your Microsoft Exchange Server installation.
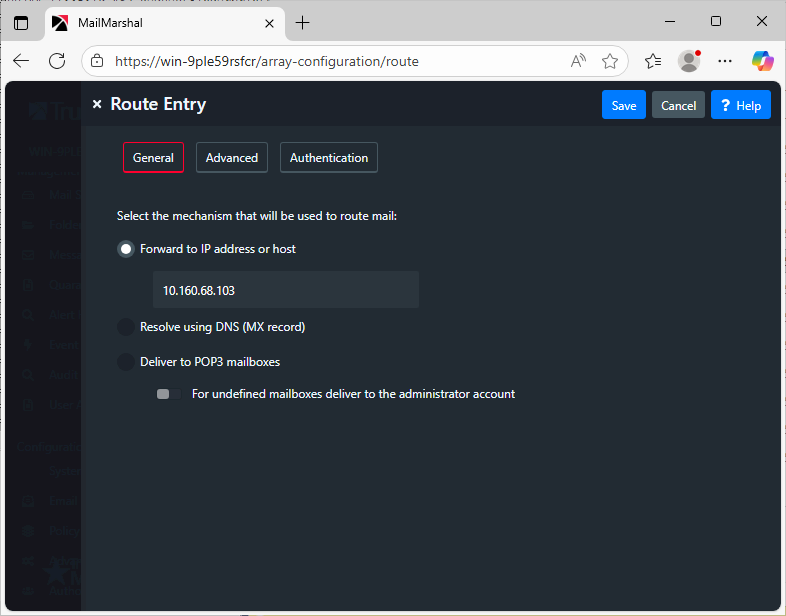
- On the Advanced tab of Route Entry Properties, make any changes to the Port and Priority for the route. For more information see Help.
- If Exchange and MailMarshal are on the same server, be sure to configure and use a unique port for Exchange. See the section about configuring Exchange below.
- You can also configure MailMarshal to make authenticated connections to Exchange. See the Authentication tab of Route Entry Properties. Details are beyond the scope of this article.
- Save the changes and commit the configuration.
Configuring MailMarshal Relaying Permissions:
In most cases the above steps will also allow Exchange Server to relay outgoing email through MailMarshal. However, if you find that relaying from the Exchange Server is denied by MailMarshal, you can allow relaying using the following steps:
- In the Management Console, expand System Configuration > Array Properties, and select Relaying.
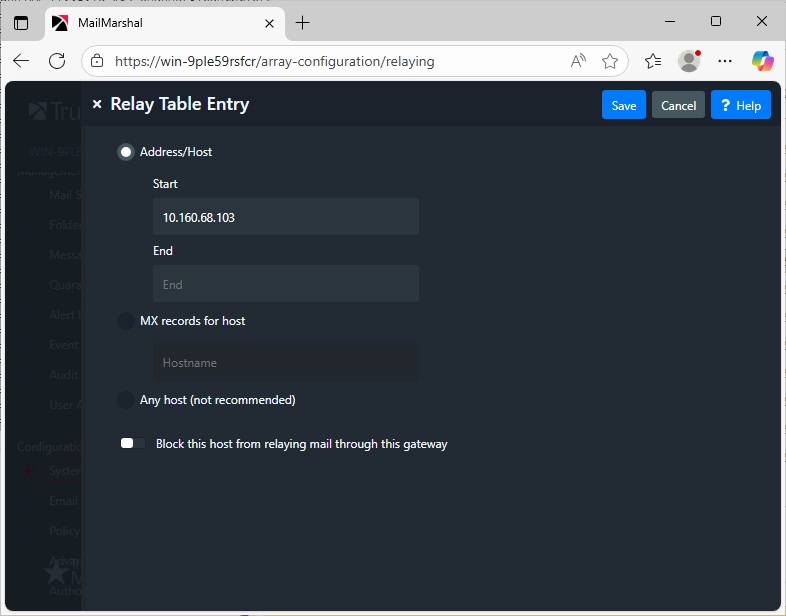
- Edit the Default Relay Table.
- Add an entry with the IP Address of the Microsoft Exchange Server you want to allow to forward email to SEG.
- Save the changes and commit the configuration.
Configuring Exchange Server
Follow the steps below to configure Microsoft Exchange Server to receive email from MailMarshal:
- In the Exchange Admin Center website, select mail flow from the left menu, and then select receive connectors from the top menu.
- From the Select server menu, select the server you want to use to receive incoming mail from MailMarshal.
- You may be able to use an existing receive connector such as the "Default Frontend" connector, or you may need to create a new connector.
- If you want to use an existing connector, double-click to edit it, and verify the network and permission settings are as described below.
- If you want to create a new connector, click + to create a new receive connector.
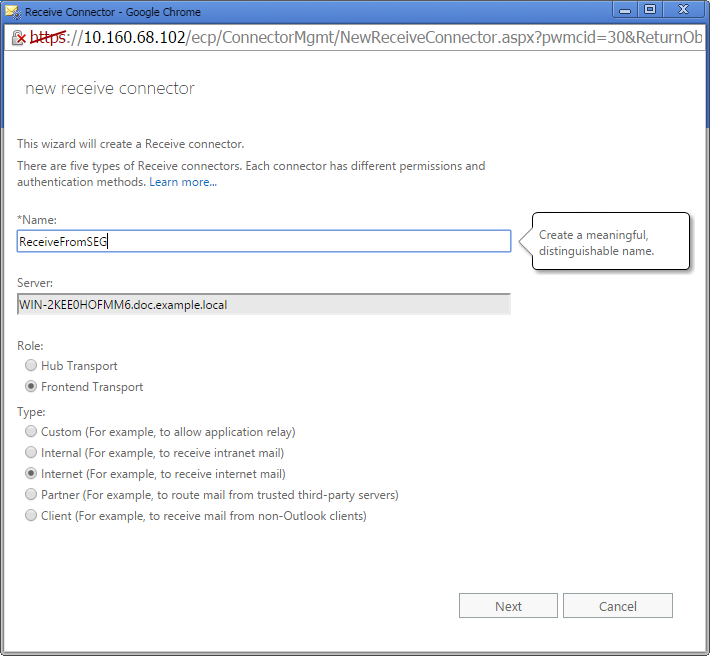
- Enter a Name for the connector.
- Select Role: Frontend Transport
- Select Type: Internet
- Note: This setting enables connections from all locations. If you want to limit connections by IP address, after creating the connector edit the setting on the Scoping tab.
- On the Network adapter bindings window, ensure the IP addresses field includes All Available IPv4. (You can also use IPv6 with current MailMarshal versions.)
- For the Port:
- If Exchange and MailMarshal are on the same server, DO NOT use port 25. Instead, edit the line and select an unused port. Port 97 is often available.
- If Exchange and MailMarshal are on separate servers, generally you should use port 25.
- Click Finish.
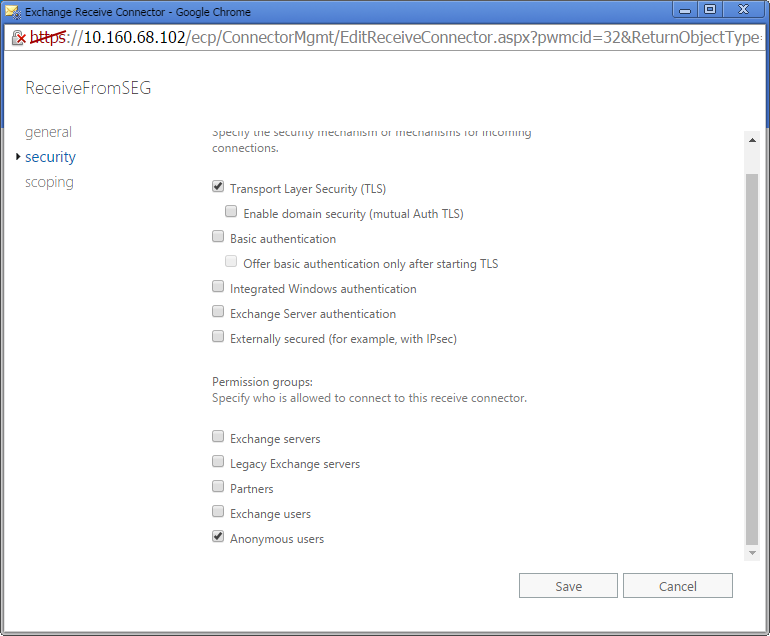
- Verify anonymous access:
- Double click the name of the new connector.
- On the Security tab, ensure the Anonymous users box is checked. Click Save.
- You can also enable or require authenticated connections from MailMarshal with other options on the Security tab. Details are beyond the scope of this article.
Follow the steps below to forward mail from Microsoft Exchange Server to MailMarshal:
- In the Exchange Admin Center website, select mail flow from the left menu, and then select send connectors from the top menu.
- Click + to create a new send connector.
- A Send Connector may already be configured. If you want to use the existing connector, verify the network and security settings as described below.
- Enter a Name for the connector and select Custom from the menu. Click Next.
- On the Network Settings window, select Route mail through the following smart hosts. Click Add and enter the IP Address where MailMarshal accepts email. Click Save and then Next.
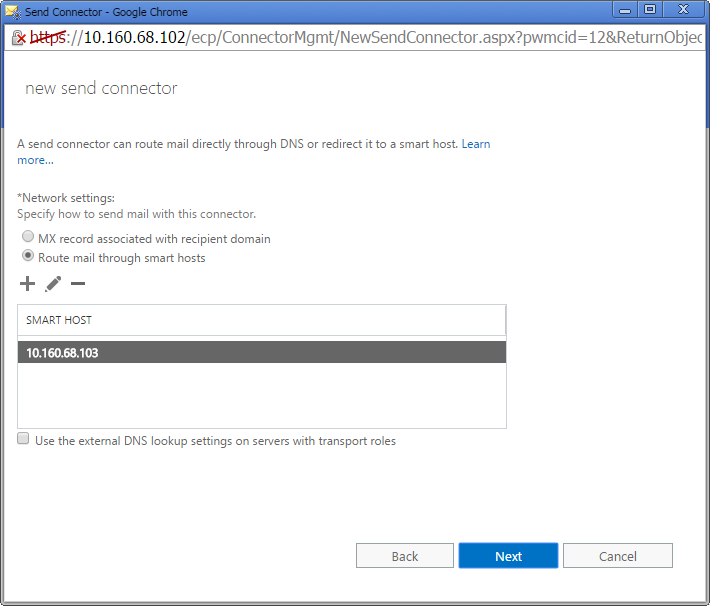
- For array installations, use the address of an email processing node or the external IP of a load balancer; for single servers, the address of the server.
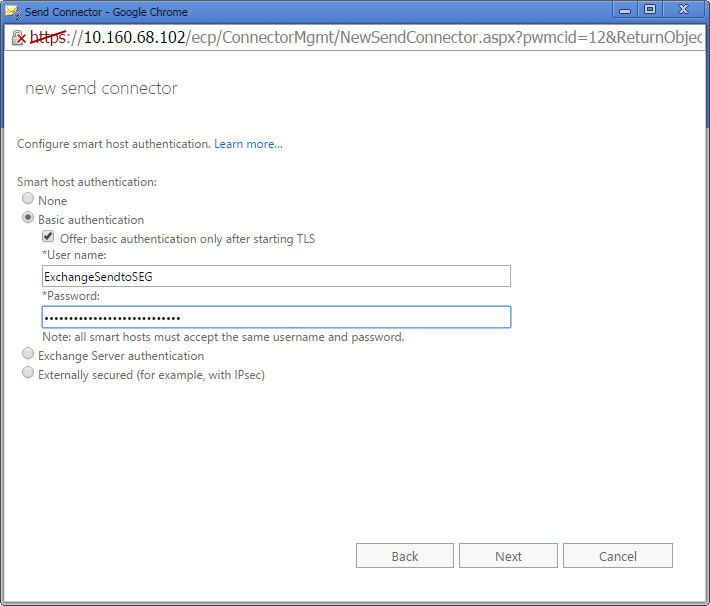
- Select an authentication method, or "none" if you do not want to require authentication. All current MailMarshal versions support Basic authentication and Basic over TLS.
- Before enabling authentication here, ensure you have set up the required account (and TLS if desired) in MailMarshal.
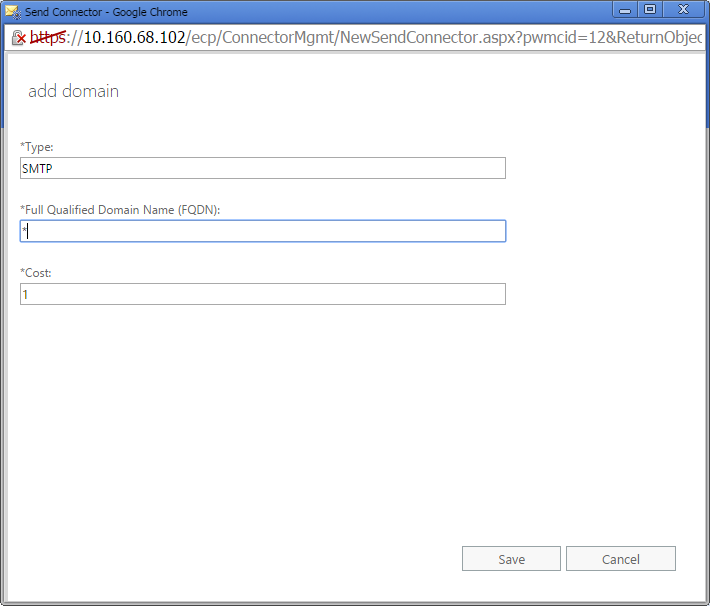
- On the Address space window, click + to add an address space. In the FQDN field, enter * to signify all domains. Click OK and then click Next.
- On the Source server window, click + to add one or more servers. Generally add all Mailbox servers in the Exchange installation. Click OK and then click Next.
- Click Finish to create the connector.